Basic Self-Help Protection Measures Reduce Threat; Villains Target Seniors by Pretending to be Helpers
A Westchester community computer non-profit is warning the public that while home computer virus threats are on the upswing, there are easy, protective measures that all of us can take. The Westchester PC Users Group (WPCUG) alerts that scammers, hackers and other bad actors increasingly employ fake emails, fake alerts that pop up when viewing legitimate websites, telephone scams and anti-virus marketers peppering cyberspace with hard-sell sales messages.
All these literally touch all the homes in the region—and particularly try to trick untrained senior citizens into downloading malicious software. WPCUG president and former career IBMer Pierre Darmon, who is a computer consultant based in White Plains, senses a false sense of security by home users who think that computer viruses are aimed only at big companies and big industry.
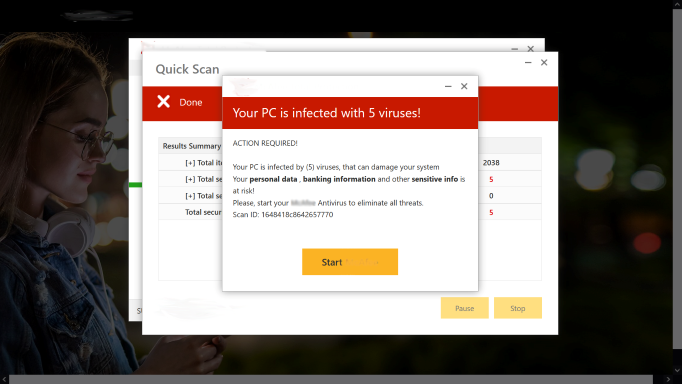
Darmon said that all home computer users on websites can encounter a takeover of their web browser software by scammers with large-size messages such as “your computer may be infected” and other chilling warnings.
“This is scary because it makes you think that you’ve lost control of your computer since it is a full-screen message,” says Darmon. “And there’s a worry that the scammers may have done some more serious damage in the background.”
In reality, the scammers have only put the user’s browser in full screen mode that makes it difficult to close the page. WPCUG advises that users can make a safe exit most of the time by pressing on their keyboards Alt-F4 (on Windows) and Cmd-Q (on macOS). That closes the browser altogether and lets users regain control of their computer; after such force-closing, the browser can then be reopened.
Browsers are software to surf the internet such as Google Chrome, Mozilla Firefox and Microsoft Edge for Windows, and Apple Safari for macOS. Malware (a contraction of the phrase “malicious software”) is software that is harmful. One type of malware is a virus, self-replicating software designed to spread from computer to computer. Viruses typically infect computers through “phishing” (think of “fishing”) whereby users accept a computer prompt ostensibly from reputable sources that really is from scammers; scammers seek unauthorized access to digital devices such as a home computer, often with the aim of hijacking online banking or credit information to make purchases.
“Once you let someone with bad intentions into your machine, it’s usually downhill from there,” says Jonathan Hauff, a computer consultant based in Larchmont NY who is a former WPCUG president and current WPCUG workshop moderator. Regarding telephone calls from scammers, “these are not nice people, though they try to sound nice on the phone. It’s a con game to them. They really are heartless criminals out to take advantage of people, especially older people” who are often too trusting.
On Jan. 27, the Federal Trade Commission (FTC) issued an alert that scams involving online social media climbed a staggering 18-fold from 2017 to 2021.
Here are a few tips to avoid the growing threats of malware and viruses:
When in doubt about a phone or computer message for a bank transaction or online purchase such as with Amazon, don’t use links or phone numbers provided. If from scammers, those connections are not legitimate. Instead, independently dial or connect to a bank/retailer website to check the real status of an account.
Beware of popups messages when browsing websites urging software updates, which are sometimes legitimate but also can be phishing disguised to download malware.
Some computer security firms say that they can remove ransomware, which may be true; but once a ransomware executes a computer takeover, just removing some of the core malware software may not unlock computers and data.
Sometimes legitimate antivirus companies blast hard-sell messages online to push consumers into buying high-price protection. WPCUG recommends simple anti-virus software from reputable companies that typically is offered in a free version to home users or upgraded “premium” version at modest cost.
In what is a rare scam from the most sophisticated hackers, computers infected by malware can be used as listening devices to literally picking up sounds keystrokes from other devices within audio range. These aim to capture passwords being typed and are referred to as an “air gap,” a reference to two computers that are not directly connected.
It’s advised to check with professionals if encountering persistent malware on personal devices, because simply making malware disappear from screens doesn’t necessary mean it’s really gone.
The bad actors are active in several areas, says George Hauss, a Yonkers resident who teaches computer classes at Westchester Community College. They “are basically trying to get information from you such as banking and other financial passwords so they can transfer money out of your accounts. Some are trying to get your personal information for marketing purposes and are more benign so you’ll just get more targeted emails, although those can drive you crazy. Others are hackers who are trying to get into your computer without your consent to extract information or install encryption programs to make the computer inaccessible, and then hold the access for ransom,” said Hauss, a WPCUG member and semi-retired chemist and computer programmer.
Hauff, when speaking to consumer groups about tech, frequently asks the audience by show of hands to see who is doing full backups frequently and also who has ever suffered important data loss. He finds the same hands go up for both questions. “Unfortunately, few people do proper backups on a regular basis unless they have experienced a major data loss themselves,” Hauff observes.
He recommends making backups of personal data as insurance in the event of data loss; this creates a copy of data as of that moment. A full backup, when installing software and external hardware storage devices, can be complicated. But just duplicating personal data is a simple with online subscription backup services and free cloud storage offered by software companies. Having a duplicate of personal photos, Word files and an address book is a blessing in the event of a data loss.
Other safety measures include:
Stay up-to-date on software updates, which will include patches to block the latest viruses.
Realize that ALL software on a home computer needs to be updated, not just the core Microsoft or Apple operating systems. For example, hackers are known to target browsers and their extensions, and specialized home management software (controlling household lights, door cameras, etc.) on smart phones.
If one does get on a phone call or computer connection that raises suspicion, immediately terminate the phone call or the online connection, which means hanging up or shutting down the computer. If challenged by a victim becoming suspicious in a phone conversation, the scammer will simply accelerate installation of malware.
It’s usually better not to respond to suspicious emails and calls (“This is Amazon notifying you that a $990 purchase billed to your account will be shipped momentarily…”) because doing so confirms to the scammer that contact information is valid. Simply disconnect. Contact Amazon to check without using links or phone numbers provided in the alarming messages.
Don’t use short, easy-to-guess passwords for online accounts, and especially don’t employ identical passwords across multiple accounts, because these are easy to hack. Multi-word phrases that are easy-to-remember (peppered with a few obscure characters) are one way can help keep track of different passwords.
Take the time to set up two-factor authentication (2FA)—security questions—on any account that offers, because that can defeat hackers.
For more information, visit the Westchester PC Users Group (https://www.wpcug.org/)





